Audio Architect allows users to connect remotely to the system over a network. This feature is intended to allow connections to devices that cannot automatically be located by Audio Architect due to network configuration or security measures.
A computer network is often divided into subnets (interconnected but independent segments or domains) in order to improve performance and security. A proxy server sits between a client application, such as a Web browser, and a server. It receives requests from a client program and forwards them to the appropriate server for the request to be satisfied. Proxy servers have two main purposes: to improve performance for groups of users and to filter user requests.
If you need to control or monitor HiQnet devices that reside on another subnet then you will need to specify the IP address for the proxy.
NOTE: Each device has its own properties and settings. Not all devices support proxy connections; see individual device help.
Crown PIP-USP3 Module - Crown PIP-USP3/CN Module
Crown I-Tech - Crown I-Tech HD - Crown Macro-Tech i Series
Crown CTs4200USP/CN - Crown CTs8200USP/CN
dbx System Core Processor 32/64
The following sections cover common ways that a proxy might be used:
1. If a DHCP server exists on the remote network, it is strongly advised that a static IP address be used for the device which will be the proxy. This ensures that the proxy device does not change its IP address due to address negotiation with the DHCP server. In order to successfully connect to a proxy device, you must know its IP address in advance of attempting the connection.
2. The proxy device must reside on the same subnet as the devices to which it will act as a proxy. For example, if all devices are on a network with IP addresses of 10.1.1.x and a subnet mask of 255.255.255.0 then the proxy device must also be in the same IP address range with a matching subnet mask.
3. A network to which a proxy will be used to connect must be set up entirely in advance. Due to the nature of using a proxy device to attach to a remote network, the Readdress Devices screen in Audio Architect will not be able to modify devices on the remote network.
4. If a firewall exists between Audio Architect and the proxy on the remote network, port 3804 must be opened for both TCP and UDP traffic to allow for Audio Architect traffic to pass unencumbered.
For accessing a HiQnet system configured as a private network behind a firewall, or for accessing a HiQnet system through a shared public infrastructure such as the Internet, we recommend that a Virtual Private Network (VPN) solution be used. VPN creates a tunnel between two networks, or between a host and a network, and provides both authentication and encryption services. There are a number of both hardware and software VPN solutions available on the market.
Steps for connecting to a proxy over a VPN connection
1. Launch VPN software on client PC and establish connection to remote network.
2. Launch Audio Architect on client PC.
3. Configure Audio Architect to use a proxy:
a. From the menu, select Q-Button > Options > Network Connectivity.
b. If "Ethernet Interfaces" says "All Adapters," select it and click "Remove Connection."
c. Click on "Add Connection" and select the IP Address of the VPN.
d. Input the IP Address of the Proxy Device
e. Once the address is highlighted, click "Add Connection."
f. Click "OK" then "Finish."
4. Close Audio Architect.
5. Launch Audio Architect again. The proxy device and other HiQnetTM compatible devices should display.
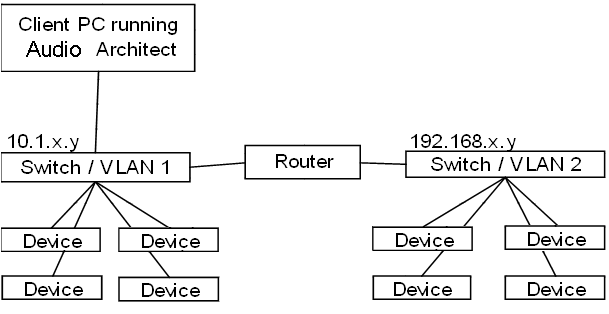
This case would be useful for running devices on separate VLANs within the same physical space. The likely reason to do this would be to isolate CobraNet traffic from a group of devices away from the larger venue as a whole.
The topology of such a network may look like the following:

In this case, VLAN 2 would contain the CobraNet or some other traffic which you wish to isolate from the larger control network (VLAN 1). The router in between the two switches will block this traffic from getting onto VLAN 1 but will allow control data to pass between the two VLANs so that the PC running Audio Architect need only be physically connected in one location.
1. The router must allow TCP and UDP data on port 3804 to flow between the two networks (required in order for meter data to display correctly).
2. Launch Audio Architect on client PC.
3. Configure Audio Architect to use a proxy. To do so, click Q-Button > Options > Network Connectivity > Add Connection. In the “Enter Proxy Connection Address” field, enter the IP address of the proxy device, and then click the “Add Connection” button.
4. Click "OK" then "Finish."
5. Close Audio Architect.
6. Launch Audio Architect again. The proxy device and other HiQnet compatible devices will should display.
This is a fail-over mechanism in case a proxy goes offline. There will still only be one "active" proxy per VLAN at a time.
Each time Audio Architect goes online, the first proxy in each comma-separated list is activated. This is the proxy list under /Options/Network Connectivity tab in SA. Commas are allowed to specify multiple proxy IP addresses per subnet.
For example:
192.168.0.123,192.168.0.124,192.168.0.125 ;Anything after a semi-colon is a comment
10.1.19.51,10.1.19.52
If an active proxy device connection fails, then the next IP address in the list become the active proxy. If all of the IP addresses in the list have been tried and failed, the software will start over with the first IP address in list.
If networking is restarted, SA always starts over at the first proxy in the list for each VLAN.
Events are written to the event log for each proxy that is successfully connected, as well as the failures.
Important safety tip: do not try to fool the list. Do not put the same IP address on different rows. Do not put proxies that really live in the same VLAN on separate rows.